Can Spider Lath Be Installed With Roofing Nails
How to install Greenbone Vulnerability Management (GVM) (formerly OpenVAS) on Kali Linux
OpenVAS is now renamed Greenbone Vulnerability Management (GVM)
When the OpenVAS projection was created, information technology only consisted of a vulnerability scanning engine. Greenbone Networks received funding shortly thereafter to provide professional person vulnerability scanning back up. Greenbone took over development leadership, added a few software components, and turned OpenVAS into a multi-pronged vulnerability management solution that withal retains the value of open and free software.
Over the years, it became apparent that the use of OpenVAS as a trademark for an open source project and funding for almost all of the project's evolution had not been appreciated from exterior. Therefore, after the release of the OpenVAS 9 platform, it was renamed Greenbone Vulnerability Management (GVM) and released as Greenbone Source Edition (GSE). Since GVM 10, the term OpenVAS is used just for the scanner component, as it was at the beginning of the project.
Greenbone Vulnerability Direction (GVM) packages: https://github.com/greenbone
Errors when installing and starting GVM, OpenVAS
During the installation and launch process, I encountered quite a few errors, which, nevertheless, were resolved. Under the supposition that these errors are common to anybody (not simply my particular installation), I described these errors right during the installation process, as a event of which the instructions became cluttered.
If during the installation process you lot do not run into the described errors, please write about it in the comments – if the errors do non appear for anybody, then I will put them at the very end of the article, due to which, in full general, the instruction will get clearer.
How to install OpenVAS (GVM)
Since the authors renamed openvas to gvm (more precisely, divided it into different packages), now the main package is gvm, when it is installed, all other necessary packages will also exist obtained as dependencies.
Installation is washed like this:
sudo apt update sudo apt install gvm
Setting upwardly OpenVAS
Let's start by setting upward the Open Vulnerability Assessment Scanner (OpenVAS) for Greenbone Vulnerability Management (GVM) solution.
It is used in Greenbone Security Director and is a full-fledged scan engine that performs constantly updated and expanded submissions of Network Vulnerability Tests (NVTs).
The scanner needs a running Redis server to temporarily store the collected data on the scanned hosts. Configuring the Redis server is done similar this (these commands need to exist executed in one case):
wget https://raw.githubusercontent.com/greenbone/openvas-scanner/master/config/redis-openvas.conf sudo cp redis-openvas.conf /etc/redis/ sudo chown redis:redis /etc/redis/redis-openvas.conf echo 'db_address = /run/redis-openvas/redis.sock' | sudo tee /etc/openvas/openvas.conf
Starting the Redis server (must exist done after every calculator restart):
sudo systemctl start redis-server@openvas.service
Or, if you like, add information technology to startup:
sudo systemctl enable redis-server@openvas.service
The Greenbone Vulnerability Management (gvmd) service acts as an OSP client to connect to and manage scanners. openvas does not human activity as an OSP service – you need the OSPD-OpenVAS module for that. Actual user interfaces (like GSA or GVM-Tools) will only collaborate with gvmd and/or ospd-openvas, not the scanner. You lot can run openvas to load plugins in Redis using the post-obit command:
sudo openvas -u
but ospd-openvas will update automatically.
Please notation that although yous can run openvas as a non-elevated user, it is recommended that you run openvas as root considering some network vulnerability tests (NVTs) crave root privileges to perform certain operations, such equally bundle spoofing. If yous run openvas as a user without permission to perform these operations, the scan results are likely to be incomplete.
Since openvas volition exist launched from the ospd-openvas process using sudo, the post-obit configuration is required in the sudoers file:
sudo visudo
add this line to allow the user running ospd-openvas to run openvas equally root
USERNAME ALL = NOPASSWD: /usr/sbin/openvas
Replace USERNAME with your Linux username.
You can discover out the username with the control:
echo $USER
If something does non work, then yous can view the log with the command:
cat /var/log/gvm/openvas.log
Configuring Greenbone Vulnerability Management (GVM)
Greenbone Vulnerability Manager is the central management service between security scanners and user clients.
It manages the storage of any vulnerability management configuration and scan results. Data, control commands, and workflows are accessed through the XML-based Greenbone Management Protocol (GMP). Scanners such as OpenVAS are controlled through the Open Scanner Protocol (OSP).
Deployment script (instead of openvas-setup):
sudo gvm-setup
This script needs to be run only once.
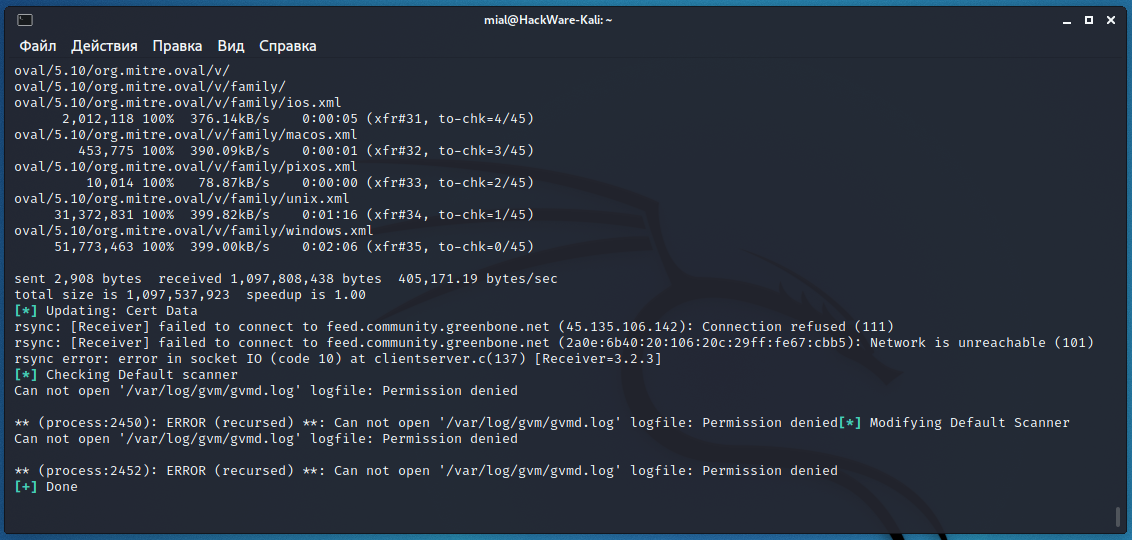
The script ended with an error:
sent two,908 bytes received 1,097,808,438 bytes 405,171.19 bytes/sec total size is 1,097,537,923 speedup is 1.00 [*] Updating: Cert Data rsync: [Receiver] failed to connect to feed.community.greenbone.net (45.135.106.142): Connection refused (111) rsync: [Receiver] failed to connect to feed.customs.greenbone.net (2a0e:6b40:20:106:20c:29ff:fe67:cbb5): Network is unreachable (101) rsync error: fault in socket IO (code ten) at clientserver.c(137) [Receiver=3.2.iii] [*] Checking Default scanner Can not open '/var/log/gvm/gvmd.log' logfile: Permission denied ** (procedure:2450): Fault (recursed) **: Tin can not open '/var/log/gvm/gvmd.log' logfile: Permission denied[*] Modifying Default Scanner Tin can not open '/var/log/gvm/gvmd.log' logfile: Permission denied ** (process:2452): ERROR (recursed) **: Can non open up '/var/log/gvm/gvmd.log' logfile: Permission denied [+] Done
Running check:
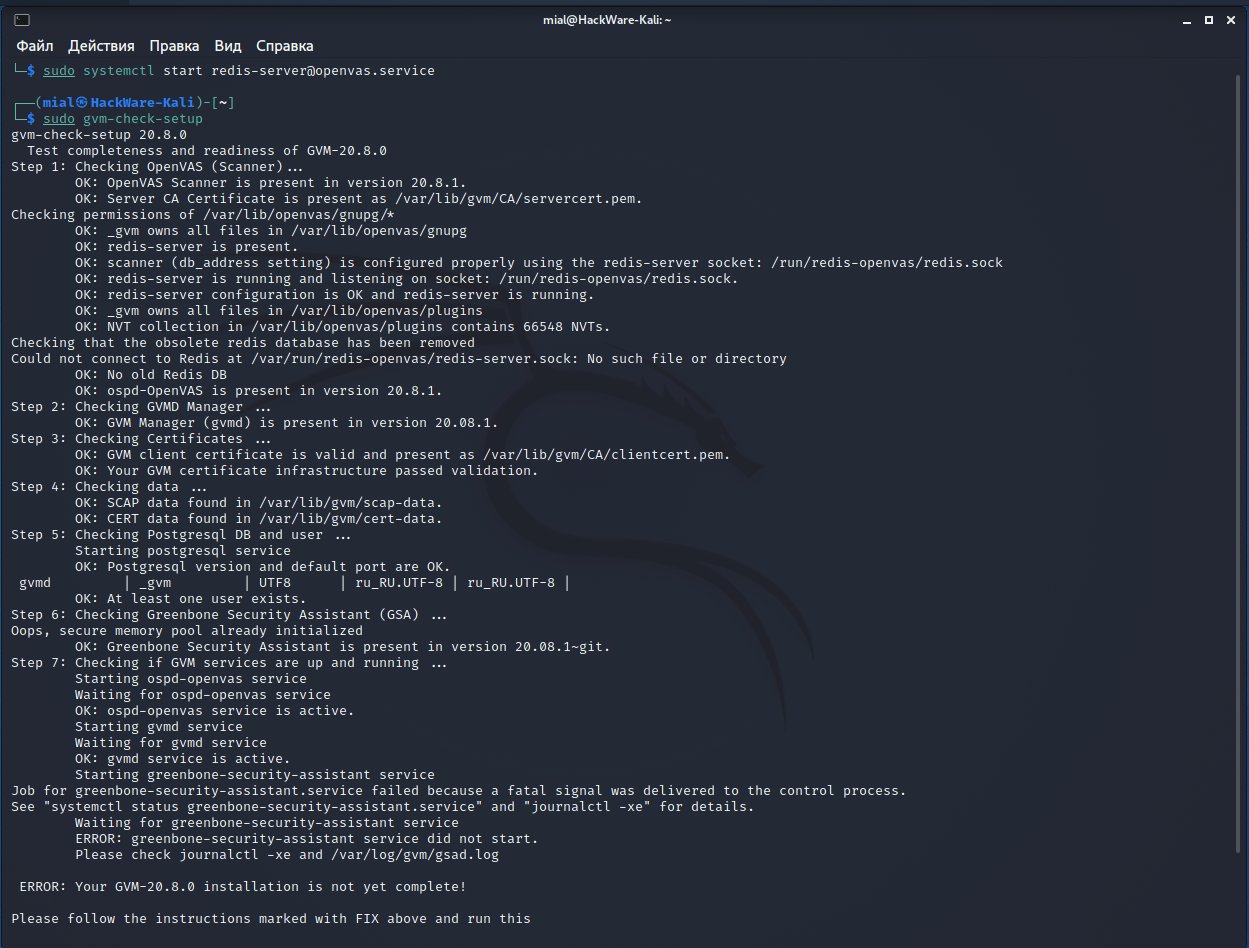
sudo gvm-bank check-setup
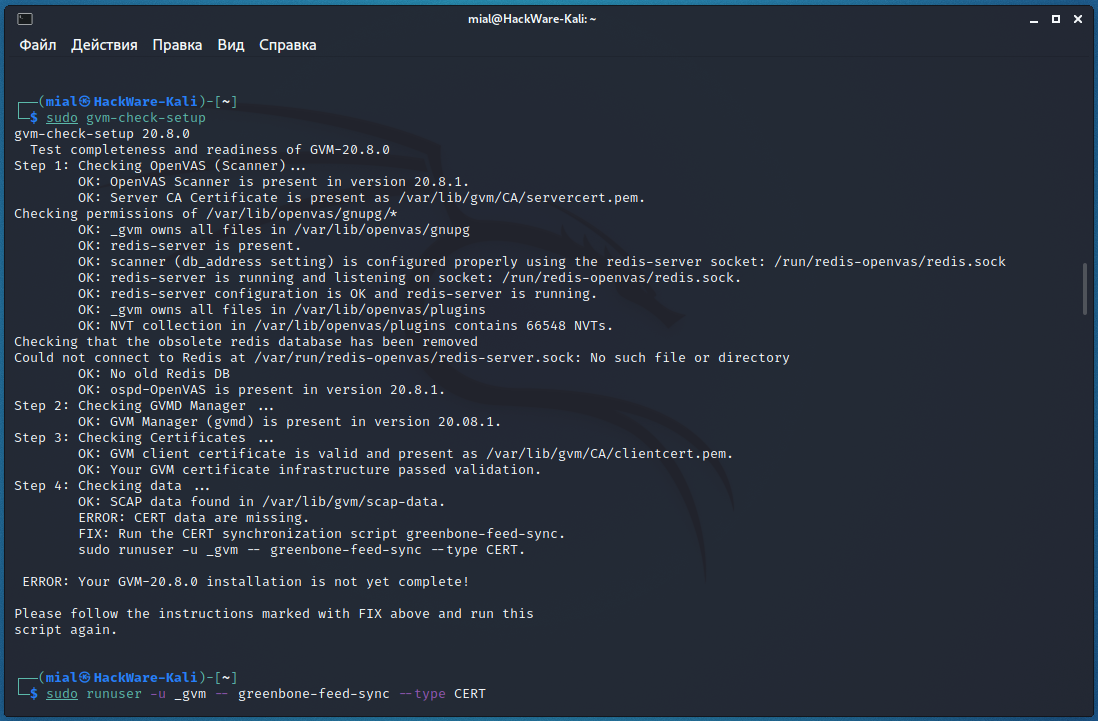
likewise showed an error in the fourth pace:
gvm-bank check-setup 20.8.0 Examination completeness and readiness of GVM-20.eight.0 Footstep ane: Checking OpenVAS (Scanner)... OK: OpenVAS Scanner is nowadays in version twenty.8.1. OK: Server CA Certificate is present as /var/lib/gvm/CA/servercert.pem. Checking permissions of /var/lib/openvas/gnupg/* OK: _gvm owns all files in /var/lib/openvas/gnupg OK: redis-server is present. OK: scanner (db_address setting) is configured properly using the redis-server socket: /run/redis-openvas/redis.sock OK: redis-server is running and listening on socket: /run/redis-openvas/redis.sock. OK: redis-server configuration is OK and redis-server is running. OK: _gvm owns all files in /var/lib/openvas/plugins OK: NVT collection in /var/lib/openvas/plugins contains 66548 NVTs. Checking that the obsolete redis database has been removed Could not connect to Redis at /var/run/redis-openvas/redis-server.sock: No such file or directory OK: No old Redis DB OK: ospd-OpenVAS is present in version xx.8.ane. Stride two: Checking GVMD Manager ... OK: GVM Manager (gvmd) is nowadays in version 20.08.1. Stride three: Checking Certificates ... OK: GVM client certificate is valid and present as /var/lib/gvm/CA/clientcert.pem. OK: Your GVM certificate infrastructure passed validation. Step 4: Checking data ... OK: SCAP data found in /var/lib/gvm/scap-data. Error: CERT information are missing. Prepare: Run the CERT synchronization script greenbone-feed-sync. sudo runuser -u _gvm -- greenbone-feed-sync --type CERT. ERROR: Your GVM-20.8.0 installation is not yet complete! Please follow the instructions marked with Gear up above and run this script once again.
To set the error "ERROR: CERT data are missing. FIX: Run the CERT synchronization script greenbone-feed-sync" run the following control:
sudo runuser -u _gvm -- greenbone-feed-sync --type CERT
Re-running the check showed an fault at the fifth step:
Pace 5: Checking Postgresql DB and user ... OK: Postgresql version and default port are OK. gvmd | _gvm | UTF8 | ru_RU.UTF-viii | ru_RU.UTF-8 | Tin can not open '/var/log/gvm/gvmd.log' logfile: Permission denied ** (process:2699): Fault (recursed) **: Tin not open up '/var/log/gvm/gvmd.log' logfile: Permission denied Mistake: No users constitute. You need to create at least one user to log in. FIX: create a user by running 'sudo runuser -u _gvm -- gvmd --create-user=<proper name> --password=<password>' ERROR: Your GVM-twenty.viii.0 installation is not all the same complete! Please follow the instructions marked with FIX above and run this script again.

There are several errors at once, only the central one is "ERROR: No users institute. You need to create at least 1 user to log in.", To fix information technology, run a command like this:
sudo runuser -u _gvm -- gvmd --create-user=<USERNAME> --password=<PASSWORD>
For example, to create a user named mial and password 2:
sudo runuser -u _gvm -- gvmd --create-user=mial --password=two
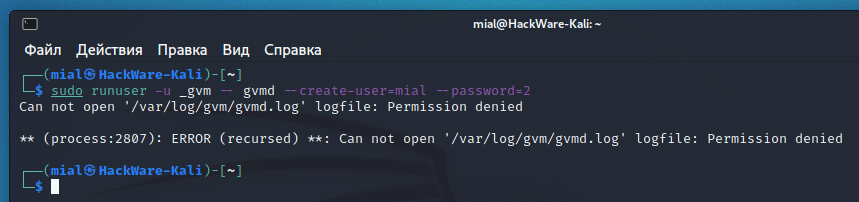
The previous command failed:
Can not open up '/var/log/gvm/gvmd.log' logfile: Permission denied ** (process:2807): Fault (recursed) **: Can not open '/var/log/gvm/gvmd.log' logfile: Permission denied
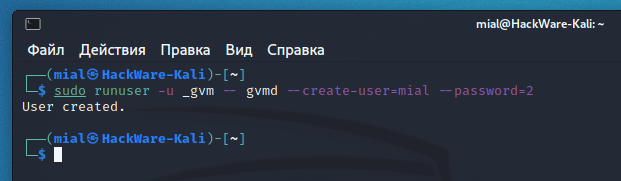
The essence of the error is that the command does non have enough permissions to write to the /var/log/gvm/gvmd.log file, even though the previous control was run with sudo. To fix the error, run the post-obit command:
sudo chmod 666 /var/log/gvm/gvmd.log
Then run the new user cosmos once more.
And i more than mistake at the 7th stride:
Footstep 7: Checking if GVM services are up and running ... OK: ospd-openvas service is active. Starting gvmd service Waiting for gvmd service OK: gvmd service is agile. Starting greenbone-security-assistant service Job for greenbone-security-assistant.service failed because a fatal signal was delivered to the control process. See "systemctl status greenbone-security-banana.service" and "journalctl -xe" for details. Waiting for greenbone-security-assistant service Error: greenbone-security-banana service did not start. Please cheque journalctl -xe and /var/log/gvm/gsad.log Fault: Your GVM-twenty.8.0 installation is not yet complete! Delight follow the instructions marked with FIX in a higher place and run this script again.
I don't know how to solve it completely, but I know how to become effectually it.
Let's move on to starting the necessary services.
Practise not forget that before starting the service you need to start the Redis server, that is, type following earlier executing the principal control:
sudo systemctl outset redis-server@openvas.service
Main service outset:
sudo gvm-first
And we become the following:
[*] Please expect for the GVM / OpenVAS services to offset. [*] [*] Y'all might need to refresh your browser once it opens. [*] [*] Spider web UI (Greenbone Security Assistant): https://127.0.0.1:9392 Chore for greenbone-security-assistant.service failed because a fatal bespeak was delivered to the control procedure. Come across "systemctl status greenbone-security-assistant.service" and "journalctl -xe" for details.

The essence of the messages is that everything started fine, except for the greenbone-security-assistant, that is, gsa, that is, Spider web UI (Greenbone Security Assistant), that is, the web interface.
You can meet the contents of the log file:
cat /var/log/gvm/gsad.log
Output:
gsad main:MESSAGE:2021-04-fifteen 09h07.55 utc:1650: Starting GSAD version xx.08.1~git gsad master:CRITICAL:2021-04-15 09h07.55 utc:1651: main: start_https_daemon failed!
https daemon failed to commencement .
gsad has a --http-only option which simply runs HTTP without HTTPS. Let's utilize it:
sudo gsad --http-only
Again, the next message will be displayed that something is wrong:
Oops, secure memory pool already initialized
However, the web interface is now available at http://127.0.0.one:9392 (but non available at https://127.0.0.1:9392!).
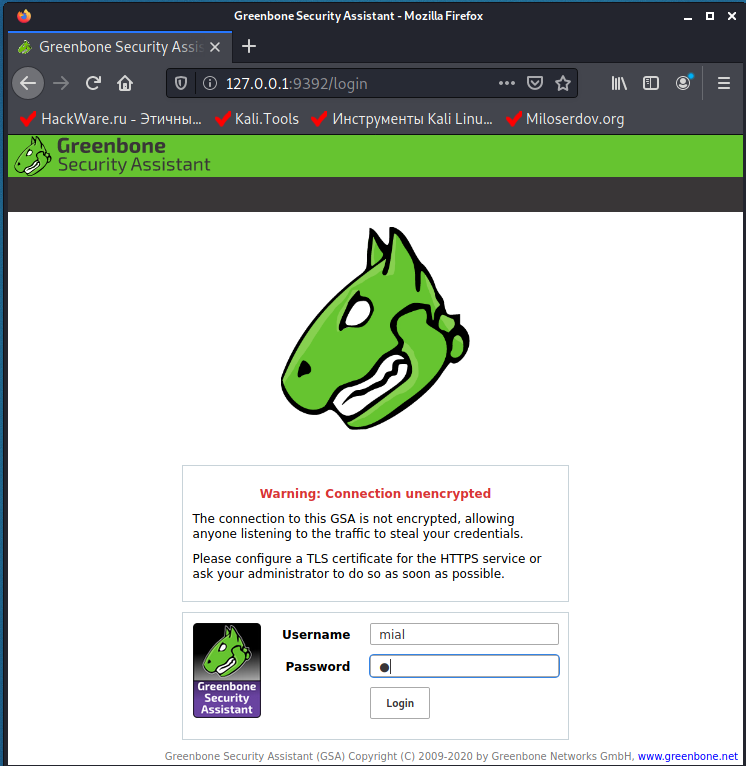
Log in using the credentials that you came upwardly with when creating a new user.
To cease the service:
sudo gvm-terminate
Other:
sudo gvm-cli sudo gvm-feed-update sudo gvm-manage-certs sudo gvm-pyshell gvm-script
In the hereafter, sometimes run the command to update signatures:
sudo runuser -u _gvm -- greenbone-nvt-sync
If something does not piece of work, so you can view the log with the command:
sudo cat /var/log/gvm/gvmd.log
Conclusion
1 of the following instructions will be devoted to how to work in Greenbone Vulnerability Direction (GVM) (formerly OpenVAS).
And do not forget to write – have you encountered the described errors during installation?
Source: https://miloserdov.org/?p=6060
Posted by: keatonhalk1956.blogspot.com


0 Response to "Can Spider Lath Be Installed With Roofing Nails"
Post a Comment